Взято с http://www.cyberciti.biz/open-source/command-line-hacks/linux-ls-commands-examples/
verything is a file under Linux and ls* and friends can help you to dig out more information from the system than you originally thought. These Linux tips may come in handy when you need to find out information quickly without going through /proc or sysfs.
#1: lsscsi
See list SCSI devices (or hosts) and their attributes under Linux operating systems:
$ lsscsi -g
Sample outputs:
[0:0:0:0] disk Adaptec RAID1-A V1.0 /dev/sda /dev/sg0 [0:1:0:0] disk SEAGATE ST373455SS 0006 - /dev/sg1 [0:1:1:0] disk SEAGATE ST373455SS 0006 - /dev/sg2 [1:0:0:0] cd/dvd TEAC DV-28E-R 1.8A /dev/sr0 /dev/sg3
#2: lsblk
Use this command to list block devices
# lsblk
Sample outputs:
NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINT sda 8:0 1 68.3G 0 disk ├─sda1 8:1 1 716M 0 part /boot ├─sda2 8:2 1 8G 0 part [SWAP] └─sda3 8:3 1 59.6G 0 part / sr0 11:0 1 1024M 0 rom
To see file system type:
# lsblk -f
Sample outputs:
NAME FSTYPE LABEL MOUNTPOINT sda ├─sda1 ext2 /boot ├─sda2 swap [SWAP] └─sda3 ext4 / sr0
To output info about permissions:
# lsblk -m
Sample outputs:
NAME SIZE OWNER GROUP MODE sda 68.3G root disk brw-rw---- ├─sda1 716M root disk brw-rw---- ├─sda2 8G root disk brw-rw---- └─sda3 59.6G root disk brw-rw---- sr0 1024M root cdrom brw-rw----
#3: lsb_release
Use this command to see Linux distribution-specific information, enter:
# lsb_release<br style=“padding: 0px; margin: 0px;” />
# lsb_release -a
Sample outputs:
LSB Version: :core-4.0-amd64:core-4.0-ia32:core-4.0-noarch:graphics-4.0-amd64:graphics-4.0-ia32:graphics-4.0-noarch:printing-4.0-amd64:printing-4.0-ia32:printing-4.0-noarch Distributor ID: CentOS Description: CentOS release 5.8 (Final) Release: 5.8 Codename: Final
#4: lsusb
Use this command to see USB buses in the Linux based system and the devices connected to them:
$ lsusb
Sample outputs:
Bus 002 Device 004: ID 045e:00db Microsoft Corp. Natural Ergonomic Keyboard 4000 V1.0 Bus 002 Device 003: ID 046d:c52f Logitech, Inc. Wireless Mouse M305 Bus 002 Device 002: ID 8087:0020 Intel Corp. Integrated Rate Matching Hub Bus 002 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub Bus 001 Device 007: ID 413c:8160 Dell Computer Corp. Wireless 365 Bluetooth Bus 001 Device 006: ID 413c:8162 Dell Computer Corp. Integrated Touchpad [Synaptics] Bus 001 Device 005: ID 413c:8161 Dell Computer Corp. Integrated Keyboard Bus 001 Device 004: ID 0a5c:4500 Broadcom Corp. BCM2046B1 USB 2.0 Hub (part of BCM2046 Bluetooth) Bus 001 Device 003: ID 0a5c:5800 Broadcom Corp. BCM5880 Secure Applications Processor Bus 001 Device 002: ID 8087:0020 Intel Corp. Integrated Rate Matching Hub Bus 001 Device 001: ID 1d6b:0002 Linux Foundation 2.0 root hub
#5: lscpu
lscpu command shows information about CPU architecture information like number of CPUs, threads, cores and much more under Linux:
$ lscpu
Sample outputs:
Architecture: x86_64 CPU op-mode(s): 32-bit, 64-bit CPU(s): 8 Thread(s) per core: 2 Core(s) per socket: 4 CPU socket(s): 1 NUMA node(s): 1 Vendor ID: GenuineIntel CPU family: 6 Model: 30 Stepping: 5 CPU MHz: 1199.000 Virtualization: VT-x L1d cache: 32K L1i cache: 32K L2 cache: 256K L3 cache: 8192K
#6: lspci
lspci command shows information about PCI buses in the system and devices connected to them:
$ lspci
Sample outputs:
00:00.0 Host bridge: VIA Technologies, Inc. VX800 Host Bridge (rev 14) 00:00.1 Host bridge: VIA Technologies, Inc. VX800/VX820 Error Reporting 00:00.2 Host bridge: VIA Technologies, Inc. VX800/VX820 Host Bus Control 00:00.3 Host bridge: VIA Technologies, Inc. VX800 PCI to PCI Bridge 00:00.4 Host bridge: VIA Technologies, Inc. VX800/VX820 Power Management Control 00:00.5 PIC: VIA Technologies, Inc. VX800/VX820 APIC and Central Traffic Control 00:00.6 Host bridge: VIA Technologies, Inc. VX800/VX820 Scratch Registers 00:00.7 Host bridge: VIA Technologies, Inc. VX800/VX820 North-South Module Interface Control 00:01.0 VGA compatible controller: VIA Technologies, Inc. VX800/VX820 Chrome 9 HC3 Integrated Graphics (rev 11) 00:02.0 PCI bridge: VIA Technologies, Inc. VX800/VX820 PCI Express Root Port 00:03.0 PCI bridge: VIA Technologies, Inc. VX800/VX820 PCI Express Root Port 00:03.1 PCI bridge: VIA Technologies, Inc. VX800/VX820 PCI Express Root Port 00:0f.0 IDE interface: VIA Technologies, Inc. VX800 Serial ATA and EIDE Controller 00:10.0 USB controller: VIA Technologies, Inc. VT82xxxxx UHCI USB 1.1 Controller (rev a0) 00:10.1 USB controller: VIA Technologies, Inc. VT82xxxxx UHCI USB 1.1 Controller (rev a0) 00:10.2 USB controller: VIA Technologies, Inc. VT82xxxxx UHCI USB 1.1 Controller (rev a0) 00:10.4 USB controller: VIA Technologies, Inc. USB 2.0 (rev 90) 00:11.0 ISA bridge: VIA Technologies, Inc. VX800/VX820 Bus Control and Power Management 00:11.7 Host bridge: VIA Technologies, Inc. VX8xx South-North Module Interface Control 00:13.0 PCI bridge: VIA Technologies, Inc. VX855/VX875/VX900 PCI to PCI Bridge 02:00.0 Ethernet controller: VIA Technologies, Inc. VT6120/VT6121/VT6122 Gigabit Ethernet Adapter (rev 82) 03:00.0 Ethernet controller: VIA Technologies, Inc. VT6120/VT6121/VT6122 Gigabit Ethernet Adapter (rev 82)
lspci command can be used to find out if a given PCI hardware is supported of by the currently running Linux kernel. In this example find out if Ethernet controller VT6120/VT6121/VT6122 from VIA Technologies is supported or not:
# lspci | grep VT6120
Sample outputs:
02:00.0 Ethernet controller: VIA Technologies, Inc. VT6120/VT6121/VT6122 Gigabit Ethernet Adapter (rev 82)<br style=“padding: 0px; margin: 0px;” />
03:00.0 Ethernet controller: VIA Technologies, Inc. VT6120/VT6121/VT6122 Gigabit Ethernet Adapter (rev 82)
he identifier in first field 02:00.0 and 03:00.0. Now use the lspci -n as follows to get result for device 02:00.0 and 03:00.0:
# lspci -n | grep ‘0[2|3]:00.0’
Sample outputs:
02:00.0 0200: 1106:3119 (rev 82) 03:00.0 0200: 1106:3119 (rev 82)
Use the model id #3119 to search driver, as follows:
# grep 3119 /lib/modules/$(uname -r)/modules.alias
Sample outputs:
alias pci:v00001106d00003119sv*sd*bc*sc*i* via_velocity
You need to use via_velocity driver for VIA networking velocity family Gigabit ethernet adapter:
# <a style=“padding: 0px; margin: 0px; color: #2361a1;” href=“http://www.cyberciti.biz/tips/how-to-display-or-show-information-about-a-linux-kernel-module-or-drivers.html">modinfo</a>
via_velocity
Sample outputs:
filename: /lib/modules/2.6.32-5-amd64/kernel/drivers/net/via-velocity.ko description: VIA Networking Velocity Family Gigabit Ethernet Adapter Driver license: GPL author: VIA Networking Technologies, Inc. alias: pci:v00001106d00003119sv*sd*bc*sc*i* depends: crc-ccitt vermagic: 2.6.32-5-amd64 SMP mod_unload modversions parm: RxDescriptors:Number of receive descriptors (array of int) parm: TxDescriptors:Number of transmit descriptors (array of int) parm: rx_thresh:Receive fifo threshold (array of int) parm: DMA_length:DMA length (array of int) parm: IP_byte_align:Enable IP header dword aligned (array of int) parm: txcsum_offload:Enable transmit packet checksum offload (array of int) parm: flow_control:Enable flow control ability (array of int) parm: speed_duplex:Setting the speed and duplex mode (array of int) parm: ValPktLen:Receiving or Drop invalid 802.3 frame (array of int) parm: wol_opts:Wake On Lan options (array of int) parm: int_works:Number of packets per interrupt services (array of int) parm: rx_copybreak:Copy breakpoint for copy-only-tiny-frames (int)
#7: lshw / lshw-gtk
lshw command finds detailed information about the hardware configuration of the server or machine:
lshw ### See hardware in a compact format## lshw -short ### Only see disks and storage controllers in the system ### lshw -class disk -class storage ### Only show all network interfaces in HTML fomrat ### lshw -html -class network ## Graphical information about hardware configuration ### lshw-gtk
Sample outputs (taken from lshw -short command):
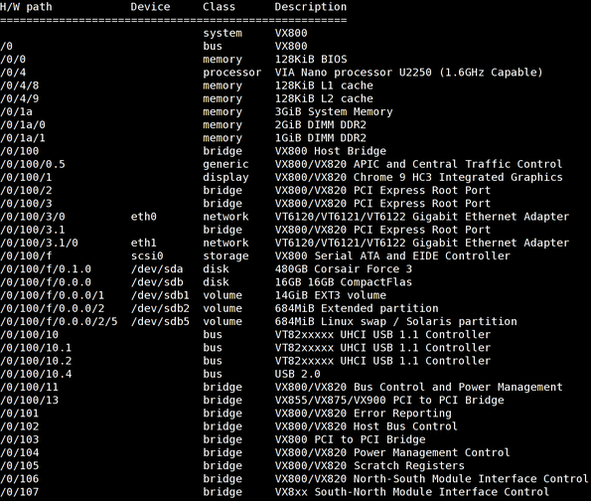 Fig.01: lshw in action
Fig.01: lshw in action
See how to use lshw command to find more information about hard disk, ram speed, pci devices and much more. You may also these Linux commands helpful which gathers up information about a Linux system and hardware.
#8: ls
Use ls command to list directory contents:
## common examples of ls, see man page more info ## ls ls -l ## long format ls -F ## appends a character revealing the nature of a file ls -a ## Show all files including hidden files ls -R ## recursively lists subdirectories ls -d ## Get info about a symbolic link or directory ls -t ## Sort the list of files by modification time ls -h ## Show sizes in human readable format ls -B ## In directories, ignore files that end with ‘~’ (backup files) ls -Z ## Display the SELinux security context ls --group-directories-first -l ## Show directories first (group directories). Useful on server. ls --color ## Colorize the ls output ls --hide='*.txt' -l ## Hide or ignore files whose names ends with .txt
#9: lsof
Use this command list open files, network ports, active processL, and much more:
### command lsof command examples ## lsof | less # List all open file lsof -u vivek -i # See all files opened by user "vivek" lsof -i 4 -a -p 7007 # List all open IPv4 network files in use by the process whose PID is 7007 lsof -i TCP:80 # Find process running on tcp port 80 lsof -i 6 # List only open IPv6 network files lsof -i 4 # List only open IPv4 network files lsof -i TCP:1-1024 # List process open in port range 1 to 1024 lsof -i @server1.cyberciti.biz:2000-2005 # List all files using any protocol on ports 2000 to 2005 of host server1.cyberciti.biz, use: lsof /dev/sr0 # List all open files on device /dev/sr0 lsof /dev/dvd # Find out why my DVD drive does not eject? lsof -i -u^root # See all files open by all users except root lsof /etc/foobar # Find out who's looking at the /etc/foobar file?
#10: lsattr
Use lsattr to lists the file attributes on a second extended file system. Can not edit or delete the file even if you are root? Use lsattr to list file:
$ lsattr /etc/passwd
Sample outputs:
------------------- /etc/passwd
Use chattr command to write protect files under Linux operating system:
# echo 'Test' > foobar<br style="padding: 0px; margin: 0px;" />
# chattr +i foobar
# lsattr foobar
Sample outputs:
----i-------------- foobar
Try to remove (delete) foobar as root user:
# rm foobar
Sample outputs:
rm: cannot remove `foobar': Operation not permitted
Remove IMMUTABLE capability i.e. file cannot be modified: it cannot be deleted or renamed, no link can be created to this file and no data can be written to the file:
# chattr -i foobar
#11: lshal
Use lshal command to display items in the HAL (Hardware Abstraction Layer) device database. HAL provides an easy way for applications to discover the hardware on the system:
# lshal | less<br style="padding: 0px; margin: 0px;" />
### get info about your hardware
# lshal -u /org/freedesktop/Hal/devices/computer
Sample outputs:
udi = '/org/freedesktop/Hal/devices/computer'
info.addons = {'hald-addon-cpufreq', 'hald-addon-acpi'} (string list)
info.callouts.add = {'hal-storage-cleanup-all-mountpoints'} (string list)
info.interfaces = {'org.freedesktop.Hal.Device.SystemPowerManagement'} (string list)
info.product = 'Computer' (string)
info.subsystem = 'unknown' (string)
info.udi = '/org/freedesktop/Hal/devices/computer' (string)
org.freedesktop.Hal.Device.SystemPowerManagement.method_argnames = {'num_seconds_to_sleep', 'num_seconds_to_sleep', '', '', '', 'enable_power_save'} (string list)
org.freedesktop.Hal.Device.SystemPowerManagement.method_execpaths = {'hal-system-power-suspend', 'hal-system-power-suspend-hybrid', 'hal-system-power-hibernate', 'hal-system-power-shutdown', 'hal-system-power-reboot', 'hal-system-power-set-power-save'} (string list)
org.freedesktop.Hal.Device.SystemPowerManagement.method_names = {'Suspend', 'SuspendHybrid', 'Hibernate', 'Shutdown', 'Reboot', 'SetPowerSave'} (string list)
org.freedesktop.Hal.Device.SystemPowerManagement.method_signatures = {'i', 'i', '', '', '', 'b'} (string list)
org.freedesktop.Hal.version = '0.5.14' (string)
org.freedesktop.Hal.version.major = 0 (0x0) (int)
org.freedesktop.Hal.version.micro = 14 (0xe) (int)
org.freedesktop.Hal.version.minor = 5 (0x5) (int)
power_management.acpi.linux.version = '20110623' (string)
power_management.can_hibernate = true (bool)
power_management.can_suspend = true (bool)
power_management.can_suspend_hybrid = true (bool)
power_management.is_powersave_set = false (bool)
power_management.quirk.dpms_on = true (bool)
power_management.quirk.vbe_post = true (bool)
power_management.type = 'acpi' (string)
system.board.product = '0R1203' (string)
system.board.serial = '.XXXXXXX.CN4864304M0335.' (string)
system.board.vendor = 'Dell Inc.' (string)
system.board.version = '' (string)
system.chassis.manufacturer = 'Dell Inc.' (string)
system.chassis.type = 'Portable' (string)
system.firmware.release_date = '12/06/2011' (string)
system.firmware.vendor = 'Dell Inc.' (string)
system.firmware.version = 'A08' (string)
system.formfactor = 'laptop' (string)
system.hardware.primary_video.product = 1567 (0x61f) (int)
system.hardware.primary_video.vendor = 4318 (0x10de) (int)
system.hardware.product = 'Precision M6500' (string)
system.hardware.serial = 'XXXXXXX' (string)
system.hardware.uuid = 'ZZZZC-XXXXXXX-104C-XXXXXXX-YYYYY' (string)
system.hardware.vendor = 'Dell Inc.' (string)
system.hardware.version = '' (string)
system.kernel.machine = 'x86_64' (string)
system.kernel.name = 'Linux' (string)
system.kernel.version = '3.2.0-0.bpo.1-amd64' (string)
system.kernel.version.major = 3 (0x3) (int)
system.kernel.version.micro = 0 (0x0) (int)
system.kernel.version.minor = 2 (0x2) (int)
#12: lsinitramfs
Use this command to show the content of given initramfs images. It allows one to quickly check the content of one (or multiple) specified initramfs files. This is useful to find out of if a given driver (such as RAID device driver) included in initramfs images or not:
lsinitramfs /boot/initrd.img-$(uname -r) # See initramfs content of current running Linux kernel lsinitramfs /boot/initrd.img-$(uname -r) | grep 'dm-' # Find out if transparent encryption / decryption driver included or not
Sample outputs (it means I can encrypt entire hard disk under Linux and support included at the boot time):
lib/modules/2.6.32-5-amd64/kernel/drivers/md/dm-snapshot.ko lib/modules/2.6.32-5-amd64/kernel/drivers/md/dm-crypt.ko lib/modules/2.6.32-5-amd64/kernel/drivers/md/dm-mirror.ko lib/modules/2.6.32-5-amd64/kernel/drivers/md/dm-region-hash.ko lib/modules/2.6.32-5-amd64/kernel/drivers/md/dm-mod.ko lib/modules/2.6.32-5-amd64/kernel/drivers/md/dm-log.ko
#13: lsmod
Use this command to list all device driver loaded currently in the Linux Kernel:
# lsmod
Sample outputs (taken from my Asus RT-16 router running on open source Tomato firmware)
Module Size Used by Tainted: P ohci_hcd 21552 0 ehci_hcd 40752 0 ext2 67712 0 ext3 136576 0 jbd 62080 1 ext3 mbcache 7280 2 ext2,ext3 usb_storage 50048 0 sd_mod 27440 0 scsi_wait_scan 960 0 scsi_mod 105376 3 usb_storage,sd_mod,scsi_wait_scan usbcore 147344 4 ohci_hcd,ehci_hcd,usb_storage nf_nat_pptp 2592 0 nf_conntrack_pptp 6000 1 nf_nat_pptp nf_nat_proto_gre 2128 1 nf_nat_pptp nf_conntrack_proto_gre 4160 1 nf_conntrack_pptp wl 1884144 0 igs 17936 1 wl emf 22720 2 wl,igs et 59744 0
To find out if you are running the module called ath_pci, enter (verify that module is loaded for a given device):
# lsmod | grep ath_pci
#14: lspcmcia
See information about the PCMCIA sockets and devices present in the system powered by Linux:
# lspcmcia
Sample outputs:
Socket 0 Bridge: [yenta_cardbus] (bus ID: 0000:03:01.0)
#15: lswm
USe this command to discover new wiimotes (Wii Remote) — the primary controller for Nintendo’s Wii console. It can be used with X to control the cursor and much more:
# lswm
#16: lsdvd
Use this command for reading the contents of a DVD and printing the contents to your display and dump for further processing in external applications.
lsdvd # Default output, show info in human readable lsdvd -a # See information about audio streams lsdvd -c # See chapter information lsdvd -s # See subpicture information (e.g. subtitles) lsdvd -s -t track-number lsdvd -a -t 1
Sample outputs:
libdvdread: Using libdvdcss version 1.2.10 for DVD access Disc Title: DVD_VIDEO Title: 01, Length: 00:22:01.000 Chapters: 06, Cells: 06, Audio streams: 04, Subpictures: 21 Audio: 1, Language: en - English, Format: ac3, Frequency: 48000, Quantization: drc, Channels: 2, AP: 0, Content: Undefined, Stream id: 0x80 Audio: 2, Language: fr - Francais, Format: ac3, Frequency: 48000, Quantization: drc, Channels: 2, AP: 0, Content: Undefined, Stream id: 0x81 Audio: 3, Language: de - Deutsch, Format: ac3, Frequency: 48000, Quantization: drc, Channels: 2, AP: 0, Content: Undefined, Stream id: 0x82 Audio: 4, Language: en - English, Format: ac3, Frequency: 48000, Quantization: drc, Channels: 2, AP: 0, Content: Undefined, Stream id: 0x83
You can use mplayer to play dvd:
$ mplayer dvd://1 -dvd-device /dev/dvd
#17: lslk
Use this command to to lists all locks associated with the local files of the system:
# lslk
Sample outputs:
SRC PID DEV INUM SZ TY M ST WH END LEN NAME portmap 1354 254,1 4309006 5 w 0 0 0 0 0 /var/run/portmap.pid atd 2124 254,1 4309014 5 w 0 0 0 0 0 /var/run/atd.pid mysqld 2404 254,1 6824038 5242880 w 0 0 0 0 0 /var/lib/mysql/ib_logfile1 mysqld 2404 254,1 6824037 5242880 w 0 0 0 0 0 /var/lib/mysql/ib_logfile0 mysqld 2404 254,1 6824036 27262976 w 0 0 0 0 0 /var/lib/mysql/ibdata1 (unknown) 2807 254,1 4309033 w 0 0 0 0 0 / (rootfs) compiz 3398 254,1 7815224 81090 w 0 0 0 0 0 /home/vivek/.nv/GLCache/a147bc5d819e1646d5baf3c8f0a017e4/8bdcca7527c339d4/736353d788902c9e.bin compiz 3398 254,1 7815223 7668 w 0 0 0 0 0 /home/vivek/.nv/GLCache/a147bc5d819e1646d5baf3c8f0a017e4/8bdcca7527c339d4/736353d788902c9e.toc python 3427 254,1 4030467 0 w 0 0 0 0 0 /home/vivek/.hplip/hp-systray.lock chrome 3567 254,1 3956948 12288 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/Login Data chrome 3567 254,1 3957700 135782400 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/History Index 2012-06 chrome 3567 254,1 3957049 120713216 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/History Index 2012-07 chrome 3567 254,1 3956937 15605760 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/Favicons chrome 3567 254,1 3957883 1155072 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/Shortcuts chrome 3567 254,1 3957138 61657088 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/History Index 2012-08 chrome 3567 254,1 3956932 24100864 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/History chrome 3567 254,1 3957892 3702784 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/Network Action Predictor chrome 3567 254,1 3956926 552960 w 0 1073741824 0 1073742335 0 /home/vivek/.config/google-chrome/Default/Web Data chrome 3567 254,1 3956809 57344 r 0 1073741826 0 1073742335 0 /home/vivek/.config/google-chrome/Default/Archived History firefox 3575 254,1 3964960 425984 w 0 1073741824 0 1073742335 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/addons.sqlite firefox 3575 254,1 3964948 1114112 r 0 1073741826 0 1073742335 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/extensions.sqlite firefox 3575 254,1 3973490 983040 r 0 1073741826 0 1073742335 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/StumbleUpon/user6896004.sqlite firefox 3575 254,1 8364042 32768 r 0 128 0 128 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/places.sqlite-shm firefox 3575 254,1 3964949 20971520 r 0 1073741826 0 1073742335 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/places.sqlite firefox 3575 254,1 8364040 32768 r 0 128 0 128 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/cookies.sqlite-shm firefox 3575 254,1 3964961 1048576 r 0 1073741826 0 1073742335 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/cookies.sqlite firefox 3575 254,1 3964944 0 w 0 0 0 0 0 /home/vivek/.mozilla/firefox/j7nk7e8h.default/.parentlock chrome 6326 254,1 7815216 88822 w 0 0 0 0 0 /home/vivek/.nv/GLCache/a147bc5d819e1646d5baf3c8f0a017e4/8bdcca7527c339d4/bc35a2d21bc47b1d.bin chrome 6326 254,1 7815215 2676 w 0 0 0 0 0 /home/vivek/.nv/GLCache/a147bc5d819e1646d5baf3c8f0a017e4/8bdcca7527c339d4/bc35a2d21bc47b1d.toc transmission 10465 254,1 11468802 0 w 0 0 0 0 0 /home/vivek/.config/transmission/lock
#18: lsmbox
Use this command to display the number of messages in a mailbox. Both total, unread but old, and new messages can be listed, for one or several mailbox files:
lsmbox ! # Get information about your inbox lsmbox spam support family # Get information about the mailboxes spam, support, and family lsmbox ~/foo # Get information about the mailbox foo which resides in your home directory
#19: lscgroup
Use this command to list all cgroups (control groups) which a Linux kernel feature to limit, account and isolate resource usage (such as CPU, memory, disk I/O, etc.) of process groups.
# lscgroup
#20: lsdiff
Use this command to see which files are modified by a patch. o sort the order of touched files in a patch, you can use:
$ lsdiff patch | sort -u | xargs -rn1 filterdiff patch -i
To show only added files in a patch:
$ lsdiff -s patch | grep '^+' | cut -c2- | xargs -rn1 filterdiff patch -i
To show the headers of all file hunks:
$ lsdiff -n patch | (while read n file do sed -ne "$n,$(($n+1))p" patch done)
#21: lspst
Use this command to list PST (MS Outlook Personal Folders) file data. It produce a simple listing of the data (contacts, email subjects, etc):
$ lspst mypst-file
#22: lsdnssec
Use lsdnssec command to ummarizes information about DNSSEC-related files. These files may be specified on the command line or found in directories that were given on the command line. The -d flag controls the amount of detail in the lsdnssec output.
# lsdnssec file
lsdnssec displays the following information about each zone for which it collects information:
keys
Key information is shown about the keys currently in use. A bar graph is included that shows the age of the key with respect to the configured expected key-life time.
This information is collected from any .krf files lsdnssec finds.
rolling status
If any zone keys are being rolled via rollerd, then the status of the rolling state is shown. The time needed to reach the next state is also displayed.
This information is collected from any .rollrec files found by lsdnssec.
Have a favorite Linux ls* command or script? Share in the comments below.